Security Controls Traceability Matrix Template - This is where you'll determine what you want to trace and why, and collect the necessary documents. Also, remove expiry documents from links and citations. Here is the link to the aws one. Could also be called security requirements. This helps ensure that no functionality is overlooked during software testing. Identify all of the requirements needed for the project, including any processes, tasks, goals, and milestones. •considerations include whether the system is a general support system, major application, or a minor application. Web the security control verify matrix model offers a scope to confirm that suggested security requirements are examined through test cases. Once you’ve identified the security controls, you will need to. A unique id number used to identify the requirement in the requirement traceability log.
5 Key Benefits of Using a Traceability Matrix to Stay on Top and in Control of Your Project
It ensures that all security requirements are identified and investigated. Web a security requirements traceability matrix (srtm) is a grid that allows documentation and easy viewing of what is required for a system’s security. Xx/xx/xx page of project name: Web a security requirements traceability matrix (srtm) is a matrix that captures all security requirements linked to potential risks and addresses.
Requirements Traceability Matrix Excel Template
Web how to use a security control traceability matrix template 1. Srtms are necessary in technical projects that call for security to be included. Web requirements traceability matrix (rtm) docx: Once you’ve identified the security controls, you will need to. Web eplc template version :
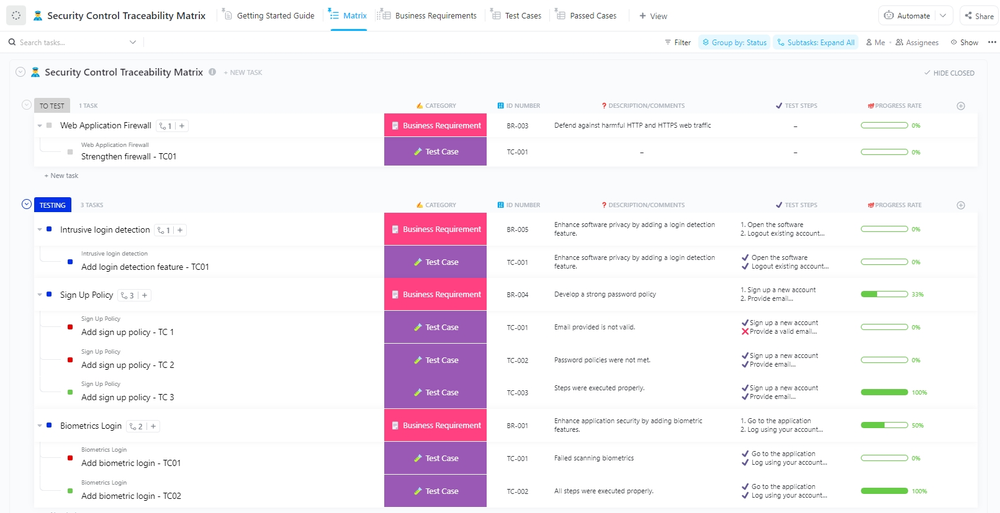
Security Control Traceability Matrix Template by ClickUp™
Once you’ve identified the security controls, you will need to. Web eplc template version : Free forever with 100mb storage. Web requirements traceability matrix (rtm) docx: This column should contain the id of any.
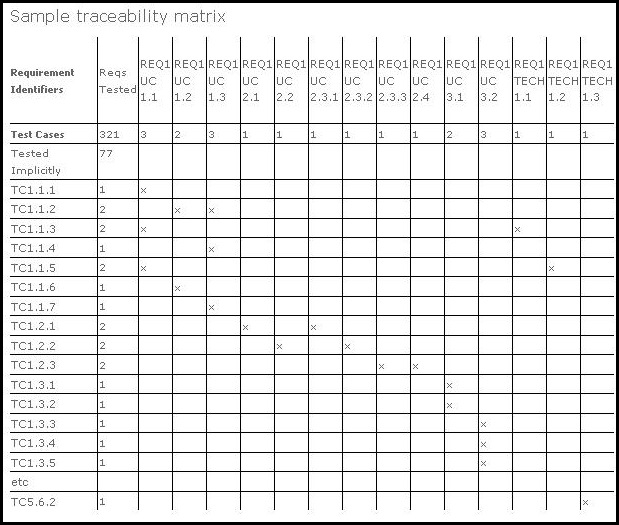
Basic Requirements Traceability Matrix Template
This column should contain the id of any. Security requirements traceability matrix (srtm) template. Web requirements traceability matrix (rtm) docx: Web a security requirements traceability matrix (srtm) is a matrix that captures all security requirements linked to potential risks and addresses all applicable c&a requirements. This helps ensure that no functionality is overlooked during software testing.
Cybersecurity Risk Assessment Template for creating cybersecurity risk assessments
Web security requirements traceability matrix (srtm) matrix documenting the system’s agreed upon security requirements derived from all sources, the security features’ implementation details and schedule, and the resources required for assessment. Xx/xx/xx page of project name: Now the excel sheet is to be created and each artifact should be added in different columns. This column should be populated with a.

TEMPLATE 2019 Update Security Requirements Traceability Matrix (SRTM) ⋆ The Cyber Sentinel
Arrange columns or fields in a way that has a clear depiction and comprehensibility. Could also be called security requirements. Security requirements traceability matrix (srtm) template. Web a security requirements traceability matrix (srtm) is a matrix that captures all security requirements linked to potential risks and addresses all applicable c&a requirements. Xx/xx/xx page of project name:

20 Critical Security Controls Spreadsheet —
Audience the principal audience for this guide includes individuals responsible for designing, managing, or deploying Web requirements traceability matrix (rtm) docx: Web eplc template version : Web here are 6 steps for using the traceability matrix template to track the progress of a project: Web how to use a security control traceability matrix template 1.
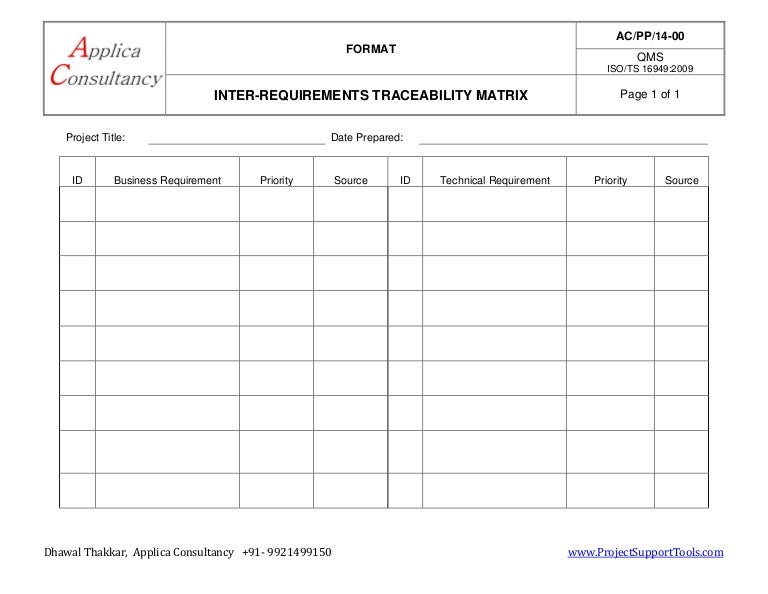
Security Requirements Traceability Matrix Template
Audience the principal audience for this guide includes individuals responsible for designing, managing, or deploying Web a security requirements traceability matrix (srtm) is a grid that allows documentation and easy viewing of what is required for a system’s security. Once you’ve identified the security controls, you will need to. To keep the traceability matrix operational and workable, avoid unnecessary documentation..

attachment_e_requirements_traceability_matrix_2.xlsx Health Insurance Portability And
Web security requirements traceability matrix (srtm) matrix documenting the system’s agreed upon security requirements derived from all sources, the security features’ implementation details and schedule, and the resources required for assessment. Web a security requirements traceability matrix (srtm) is a grid that allows documentation and easy viewing of what is required for a system’s security. Highest levels of uptime the.

Doors Traceability & View Shows Gaps In Traceability Across Modules Sc 1 St IBM
Use a doc in clickup to list out all the requirements for the project. This is where you'll determine what you want to trace and why, and collect the necessary documents. Once you’ve identified the security controls, you will need to. A unique id number used to identify the requirement in the requirement traceability log. Could also be called security.
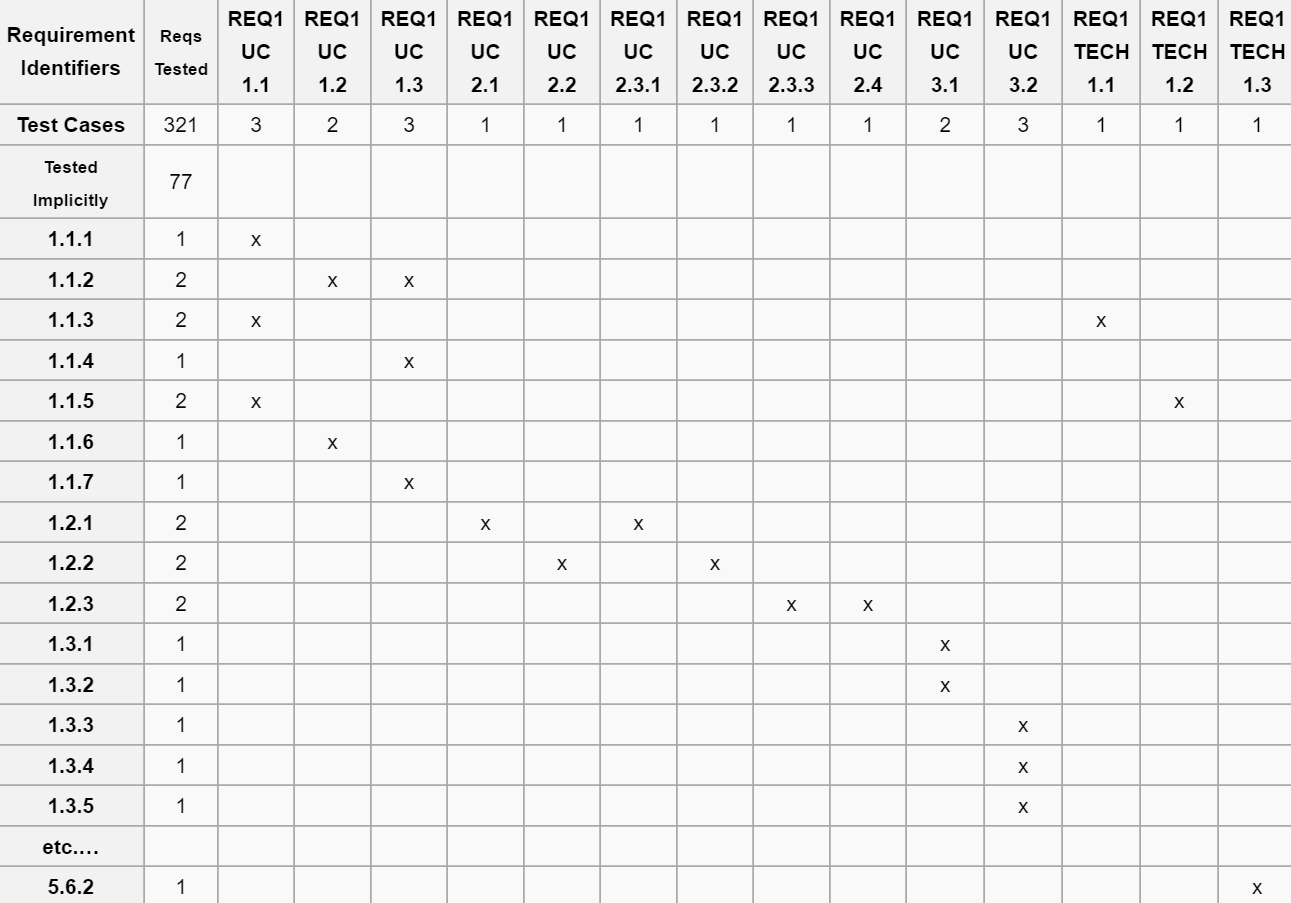
Web how to use a security control traceability matrix template 1. This column should be populated with a description of the software module(s) linked to the functional requirement. Web security requirements traceability matrix (srtm) matrix documenting the system’s agreed upon security requirements derived from all sources, the security features’ implementation details and schedule, and the resources required for assessment. Identify all of the requirements needed for the project, including any processes, tasks, goals, and milestones. Web the security control verify matrix model offers a scope to confirm that suggested security requirements are examined through test cases. Web requirement traceability matrix (scope) | complete guide to rtm. Audience the principal audience for this guide includes individuals responsible for designing, managing, or deploying Arrange columns or fields in a way that has a clear depiction and comprehensibility. Serious about security & privacy. It ensures that all security requirements are identified and investigated. Free forever with 100mb storage. Web here are 6 steps for using the traceability matrix template to track the progress of a project: Each row of the matrix identifies a specific requirement and provides the details of how it was tested or analyzed and the results. Web requirements traceability matrix (rtm) docx: 4) addition of the facts. This column should contain the id of any. Security requirements traceability matrix (srtm) template. The first step to build a requirements traceability matrix is to create the template, or shell, of your matrix. A unique id number used to identify the requirement in the requirement traceability log. Highest levels of uptime the last 12 months.